44 security labels are used in what type of model
Security Labels | Buy Custom Tamper Proof Labels | Avery | Avery Tamper-proof labels and security seal stickers are available to buy directly from the UK's leading label manufacturer, Avery. Buy blank labels to print yourself, or have them printed and supplied to your office when you use our WePrint label delivery service. We have a range of adhesive materials you can choose from, including removable paper ... Introduction to security and product protection - Labels & Labeling Figure 1.2 - Security labels and packaging can be used to protect 'assets'. It is also important to understand that security labels and security packaging in isolation cannot protect products from attacks such as counterfeiting and tampering. What they can deliver though, is a cost effective indicator that a security threshold has been ...
Security Labels: How Do They Work (And Do You Need Them?) Security labels also play a key role in assuring consumers that the genuine products they purchase have not been tampered with on their way from the maker to the consumer. Tamper evident labels are special types of labels designed to change in an obvious and irreversible way when a product is opened or if someone attempts to remove the label.
Security labels are used in what type of model
Top Applications of Security Labels Explained | PLCTX Blog Top 6 Security Label Uses. Security labels have numerous applications in everyday operations. Some of the important ones are as follows. Computer Hardware Security: Computers are perhaps one of the most valuable assets of businesses as this electronic device contains valuable and sensitive data. With the introduction of general data protection ... What are Information Security Models? - Infosecacademy.io Here some of the important models we are discussing below to understand the functions and importance of Information Security models in the current business world. Five popular and valuable models are as follows; Bell-LaPadula Model. Biba Model. Clark Wilson Model. Brewer and Nash Model. Harrison Ruzzo Ullman Model. Tamper Evident Security Labels | American Casting & Mfg. - Seals Red/White Security Labels - with Residue. Tamper evident security sticker, available in 1" x 2" and 1" x 4". When removed these labels reveal the hidden message "TAMPERED" in both the film and adhesive. Pricing is shown per roll. 1,000 labels per roll. Contact American Casting for custom colors or printing. Label Size: Required. 1" x 2" 1" x 4".
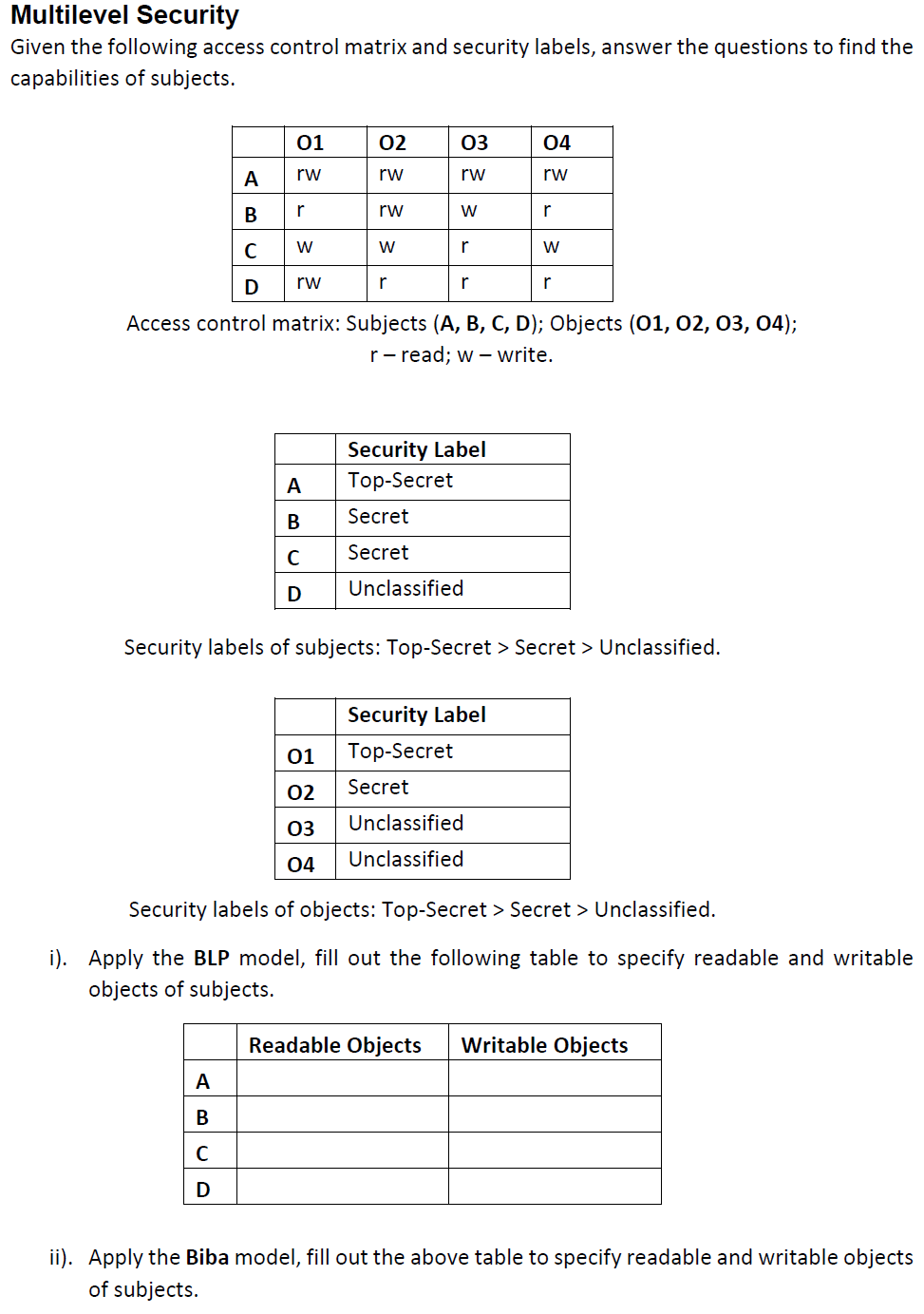
Security labels are used in what type of model. Types of Security Models | bartleby There are three main types of classic security models namely Bell-LaPadula model Biba model Clarke Wilson Security model Bell-LaPadula model This model was invented by David Elliot Bell and Leonard.J. LaPadula and therefore, this model is known as Bell-LaPadula. This model is used to ensure the confidentiality of information. Using Security Labels for Directory Access and Replication Control - Isode The access control model here is a very simple one: Directory Information has Security Labels; Users with appropriate Security Clearance can access this information. This overall simplicity is a key feature and benefit of this approach to access control. Where a security model is simple, there is less risk of user or administrator error. What is the use of security labels? - Quora Answer (1 of 2): Nowadays, security is a major concern for any reputed company to prevent their products and services from the threat of counterfeiting and duplication. So is the growing need for holograms & holographic security labels. More and more manufacturers are turning towards holograms f... Security Labels - Hologram Dome Labels Manufacturer from Bengaluru Security Labels are the most effective and commonly used product for Brand Authentication, and Brand Promotion. Since this holographic technology is in label form it can be used on any product or commodity. Holograms are very easy to Apply and use -Just remove and Paste. These labels can be supplied either manually or by auto application...
Security-labels - FHIR v4.3.0 - Health Level Seven International The Security Label vocabulary has three patterns of use: (1) Bundle: Security/Privacy considerations of a data set, (2) Context: Describe security/privacy context of a request for data, and (3) Meta Data: to indicate security/privacy meta about that data. Bundle: A bundle is a container for a collection of data. What are the features of security labels? - Quora What are the features of security labels? That depends on what you want to know. The labels themselves are just numbers, used to index a table of other ... Which of the following is the access control model ... - Skillset This access control system is based on security labeling for security clearances of users and where resources have security labels containing a data ... Security Labels and Stickers | Different Types | SecurityTags.com For high-volume, low-value stock, security labels and stickers are the ideal method of protecting products from theft. Affordable and suited to single use, they harness the power of Electronic Article Surveillance but can be easily applied and quickly deactivated at the point of sale. But how do you know which label is best suited to your needs? Here's an insight into the different types of security labels available and the products they best suit.
Security Labels - PolyLabel.com Security labels are used in an environment where you might have the necessity to identify any label tampering. There are many uses for these labels. For example, they can be used on packaging, to track data, seal freight, cargo containers, seal forensic samples, or be used in the government as a security seal. Why Are Security Labels Used CISSP Exam Cram: Security Architecture and Models The reference monitor can be designed to use tokens, capability lists, or labels. Tokens—Communicate security attributes before requesting access. Capability lists—Offer faster lookup than security tokens but are not as flexible. Security labels—Used by high-security systems because labels offer permanence. This is provided only by ... CISSP Exam Cram: Security Architecture and Models The Information Flow model consists of objects, state transitions, and lattice (flow policy) states. The real goal of the information flow model is to prevent unauthorized, insecure information flow in any direction. This model and others can make use of guards. Guards allow the exchange of data between various systems. Noninterference Model 15 facts about security labels - SecurityTags.com Security labels are another component of the loss prevention strategy known as electronic article surveillance. Like security tags, these labels are affixed to products and guard them against theft. Labels are highly affordable, quickly applied and deactivated rather than removed at the Point of Sale. Widely used
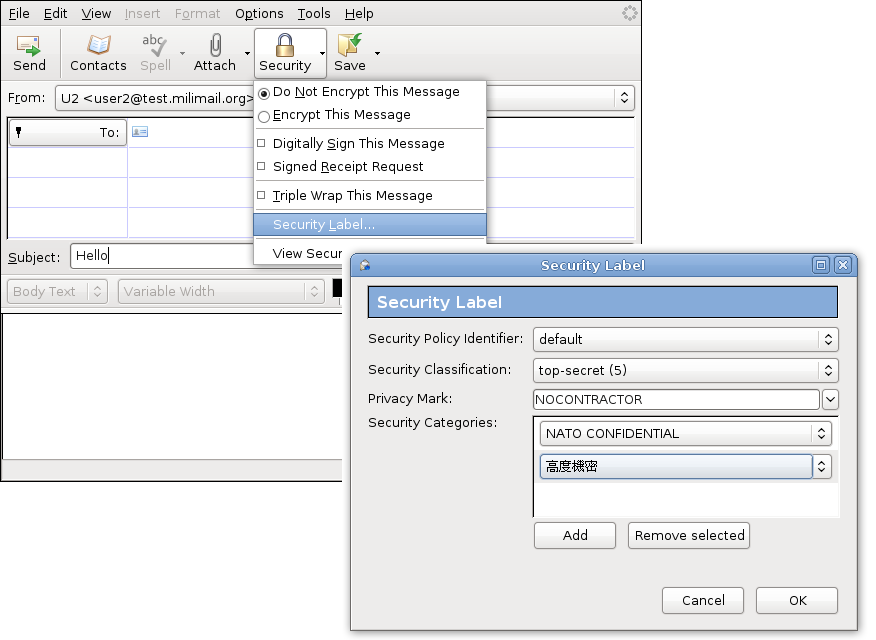
Access Control using Security Labels & Security Clearance - Isode ESS Security Labels are used in S/MIME (the Internet Standard for secure documents and email) and within STANAG 4406 (military messaging). X.411 and X.500 directory use a definition that is very similar, and is used by X.500 directory and by X.400 messaging. The rest of this document refers to Security Labels, as online representations conformant to these specifications.
Security Labels & Tags | Anti-Tamper Protection by Seareach® Our current tamper evident security stickers for computers come in the following types: 1. Type 1: White Permanent Security Label. This material is fully synthetic and comes with an aggressive adhesive that gets stronger over time. Once applied, these permanent labels are very difficult to remove and will come off in very small pieces if ...
What are security labels? | Security Labels Definition - Label Planet This could be by acting as a visual deterrent, tracking the location of the object, preventing counterfeiting, or providing visual proof that the label (and therefore the object) has been tampered with. In labelling, the term security label is applied specifically to labels that provide evidence of tampering (tamper evident labels) - although they may perform other security functions as well.
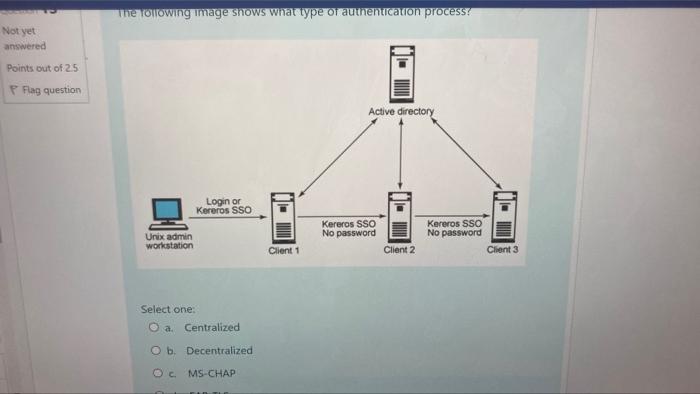
Which type of access control model assigns security level labels to ... Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the strictest access control and is typically used in military or mission critical applications. More Questions: IoT Sec 1.1 Fundamentals: IoT Security Final Exam Answers
Custom Security and Asset Labels with logos and barcodes Our two standard sizes are 47mm x19mm and 25mm x 12.5mm. In addition, each label order includes: Free Company Logos Included Barcodes & Serial Numbers Bespoke Custom Labels Layout Design Service 3 Day Turnaround on Standard Orders Low minimum orders - only 100 labels
Implementing Access Control Models - Get Certified Get Ahead 1 Sept 2017 — Q. An organization has implemented an access control model that enforces permissions based on data labels assigned at different levels. What ...
IoT Sec 1.1 Fundamentals: IoT Security Final Exam Answers 50. Match the question to one of the three contributors to the determination of risk when performing a risk assessment. (Not all options are used.) IoT Security (Version 1.0) - IoT Fundamentals: IoT Security Final Exam 22. Explanation: The three factors of vulnerability, threat, and asset contribute to determining the level of risk in risk ...
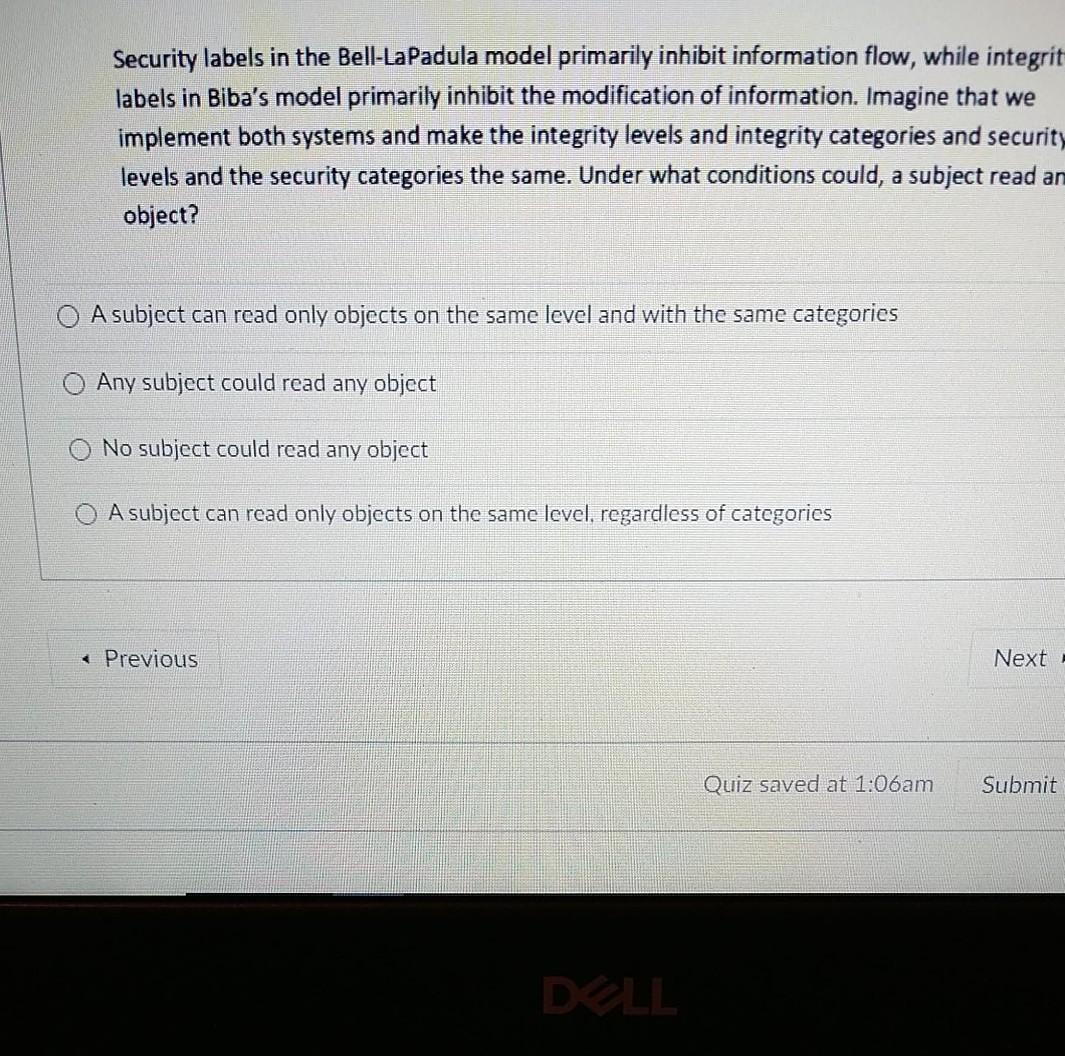
Automating System Security with AADL: 11 Rules for Ensuring a Security ... The Bell-LaPadula model requires that security labels of subjects and objects in a system are consistent with the simple security property and the star property. In addition, the semantics of AADL require that several additional properties be enforced for the security modeling to make sense.
Applications of Security Labels - JW Products Security Labels can also be used to determine if sold goods have been modified in any way that would compromise the warranty of the product. Asset Management: As well as their excellent security features, security labels can also be used for equipment tracking purposes and asset management purposes. A security label can feature a barcode, a company name or even just a number for asset tracking purposes.
What are the features of security labels? - Quora What is the use of security labels? Security labels have a lot of great uses depending on your specific needs.Custom tamper proof stickers and labels are a category of security products designed to indicate or prevent lifting and removal. Use cases include: Prevent a price tag from being moved from one product to another
LBAC security label components overview - ibm.com There are three types of security label components: TREE: Each element represents a node in a tree structure ARRAY: Each element represents a point on a linear scale SET: Each element represents one member of a set The types are used to model the different ways in which elements can relate to each other.
Security Labels, Stickers & Seals Anti Tamper - NovaVision Security labels and stickers provide an anti-tamper seal for file cabinets, doors, windows, equipment, boxes, and many other containers. All of our security labels have pressure-sensitive adhesive -- just peel and stick. Protect Your Products and Equipment Control Access to Files, Doors, & Containers Indicates Tampering or Pilfering
Security Architecture and Design/Security Models - Wikibooks Security Models. A security policy is a document that expresses clearly and concisely what the protection mechanisms are to achieve. Its a statement of the security we expect the system to enforce. it states the rules that constitute the policy. Models can capture policies for confidentiality (Bell-LaPadula) or for integrity (Biba, Clark-Wilson ...
Tamper Evident Security Labels | American Casting & Mfg. - Seals Red/White Security Labels - with Residue. Tamper evident security sticker, available in 1" x 2" and 1" x 4". When removed these labels reveal the hidden message "TAMPERED" in both the film and adhesive. Pricing is shown per roll. 1,000 labels per roll. Contact American Casting for custom colors or printing. Label Size: Required. 1" x 2" 1" x 4".
What are Information Security Models? - Infosecacademy.io Here some of the important models we are discussing below to understand the functions and importance of Information Security models in the current business world. Five popular and valuable models are as follows; Bell-LaPadula Model. Biba Model. Clark Wilson Model. Brewer and Nash Model. Harrison Ruzzo Ullman Model.
Top Applications of Security Labels Explained | PLCTX Blog Top 6 Security Label Uses. Security labels have numerous applications in everyday operations. Some of the important ones are as follows. Computer Hardware Security: Computers are perhaps one of the most valuable assets of businesses as this electronic device contains valuable and sensitive data. With the introduction of general data protection ...








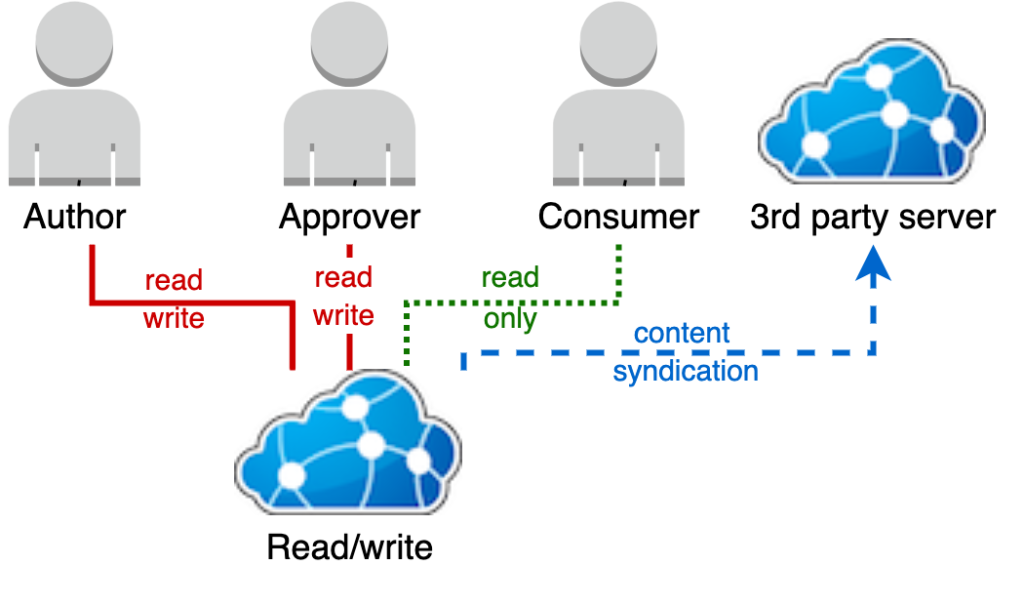
![PDF] Security model for resource availability - subject and ...](https://d3i71xaburhd42.cloudfront.net/5fa21f5740065e5adbe4ded753ed462033314858/2-Figure1-1.png)

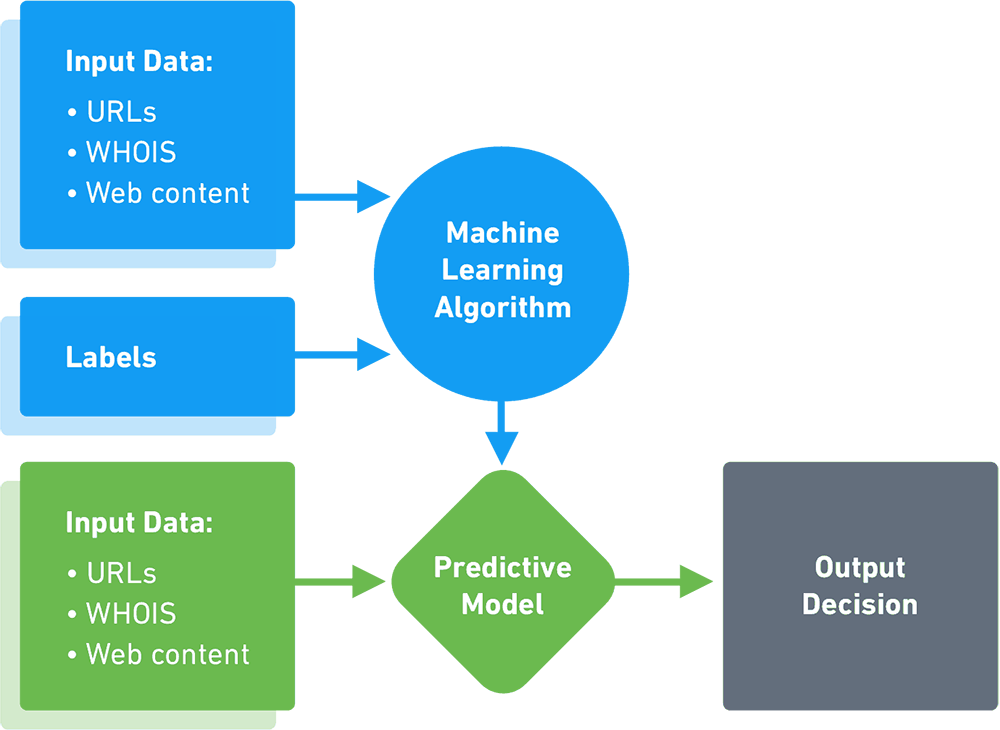










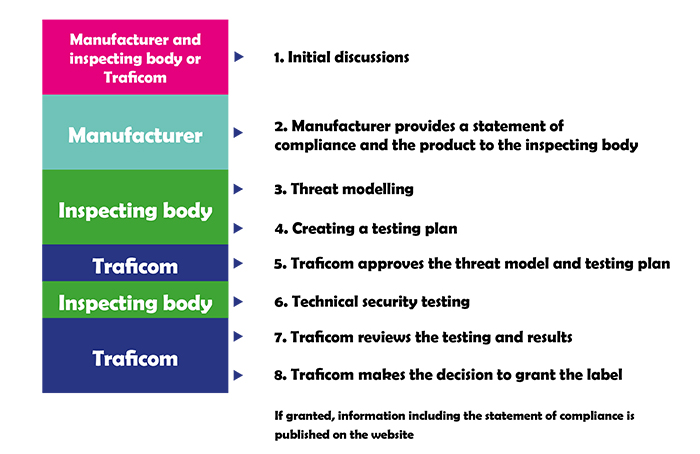


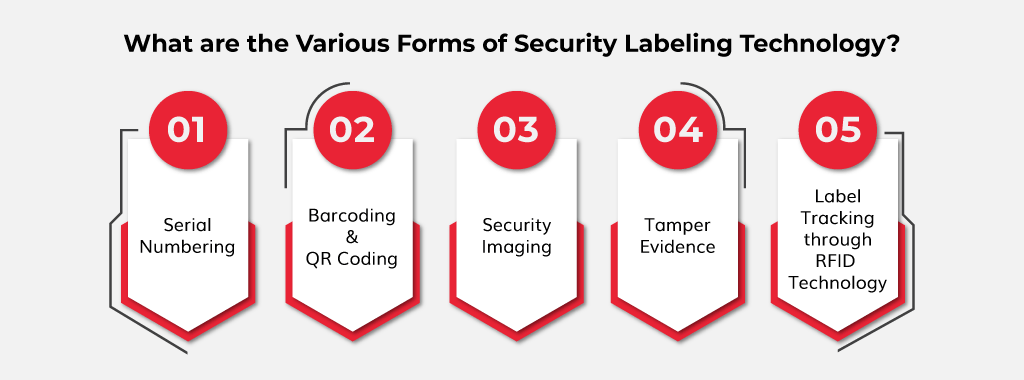







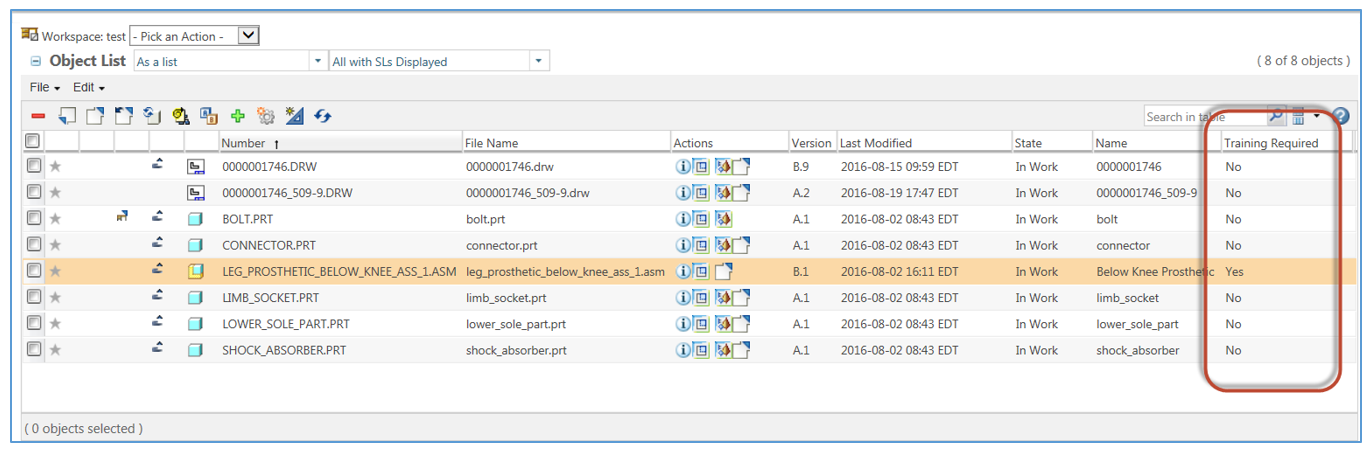

Post a Comment for "44 security labels are used in what type of model"